BugéDex
The Art of Bug Bounty, Bug Bash and Reporting

✨✨✨Greetings!✨✨✨
This blog is about my personal experience at BugéDex workshop and discovery of a great treasure.
Brief Intro:
It was a cyber security workshop based on bug bounty hunting. The event was made possible by CloudSEK & CSI-VIT Teams. It was conducted in multiple sessions that included a practical hands-on and blogging competition at the end.

😏 If you think, it was just an another spoon-feeding bugie hunting workshop, you were wrong. Ok, then let’s hop into it!
Workshop:
Speakers:
- Syed Shahrukh Ahmad ~ [ CTO, BeVigil @ CloudSEK ]
- Sai Ahladini Tripathy ~ [ Engineering Manager @ CloudSEK ]
- Sudipta Pandit ~ [ Security Engineer @ CloudSEK ]
The workshop sessions were about, the basics of SDLC & various testings, types of vulnerabilities, use-cases, OWASP Standards for Web Application & Mobile Securities, importance of writing quality bug reports, Triage back-end process, approach to bug hunting programs, etc.
Wow, that was quite a lot of topics to be taken in detail, in two hours.

The sessions were outstanding. For a tree to hold firmly over a mountain, it’s root must be strong and that was the agenda of that workshop. Also, thanks to Sai Ahladini Tripathy, for making the workshop very interactive.
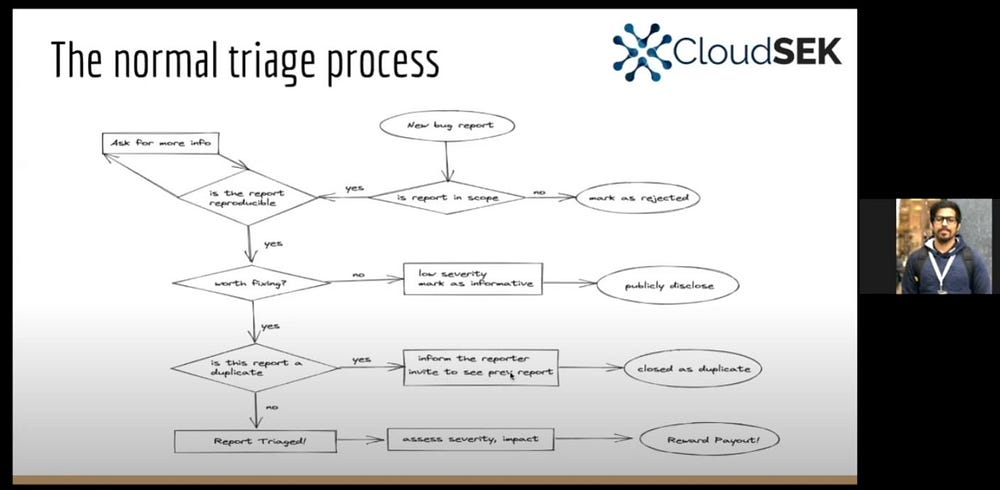
The speakers presented the important things in detail with clear examples that were very useful for a budding bug hunter and also for cyber security enthusiasts who were interested to step into application security.
One of the crucial part of the workshop sessions was the Question/Answer Session. The participants were open to post or ask any kind of related doubts. As most of the participants were new to this domain, they asked various out-of-box questions 😃
Syed Shahrukh Ahmad didn’t hesitate to repeat the presentation slides again and made to understand them properly 👌. Also Sudipta Pandit explained the OWASP Top 10 for Web App & Mobile. Thus marking the end of the first session of the workshop.
BugBash:
The second session was practical hands-on.
Syed Shahrukh Ahmed had presented an introductory session to CloudSEK’s BeVigil web application. An indigenously developed AI-based security search engine for mobile application by CloudSEK.
Initially, I thought that we would be given a key and needed to find a treasure trove. But on the contrary, we were handed over the treasure itself. Yes, it’s the BeVigil application!

Once you start to explore that search engine, you can’t just keep out digging using that technology. You will be astonished by exploring the features of BeVigil.
The working of BeVigil is fairly a simple and straightforward process:
Step 1: Sign-up using email, then simply search for an app name, developer email using the advanced filters. Or choose to directly upload any application files to the platform

Step 2: BeVigil’s mobile application scanner in the background instantly finds discovers vulnerabilities and secrets in that app as well as its metadata

Step 3: Displays search results — instantly see the risk score, security report and other relevant app data

This is the first security search engine of this kind, for mobile applications.
People who are concerned about the mobile applications that they install in their smartphones, should make use of this technology to know about those apps in a better perspective.
Let’s BASH de BUGS!

The participants were asked to use the BeVigil platform during the BugBash to find any vulnerabilities or sensitive information of any mobile application and to make & submit a proof-of-concept. Depending on number of reports submitted and its quality, the LEADERBOARD will be updated.

Soon after the introductory session, I signed-up to the BeVigil website and started to implement that was explored during the previous sessions.
👉 Firstly, I tested the mobile applications that are present in my smartphone.

🤦♂️Later I regretted it, after knowing that many of the applications used on a daily basis have risky device permissions and a lot of trackers. Then moved on to try the other mobile applications that are used on a regular basis by other users.
But soon, 😃 I discovered Twitter OAUTH Token and Secret, that were hardcoded into a mobile app and also verified those credentials as valid. If you come across any type of Twitter Oauth keys, you can use the following method to verify,

Keeping in mind about quality report writing, I created a well structured POC for that issue and submitted it.
On persistent bugbashing , I found the same issue in 5 different mobile applications that are having thousands of user downloads from Google Play Store.
Guess what, all the discovered credentials were found to be valid and BOOM! Again I started to write POCs of them. The thing was, there was a slight improvement on each time when writing the POC report. The last POC report submitted was better than the first one in terms of quality.
Thanks to Syed Shahrukh Ahmad 👍, for the session in writing quality bug reports.

That’s not the end. While exploring the BeVigil platform, I came across their blog post titled “Mobile Apps Exposing AWS Keys Affect 100M+ Users’ Data”.💡 Later on, I discovered the hardcoded AWS Credentials of a mobile app using the BeVigil platform after getting inspired by their blog.
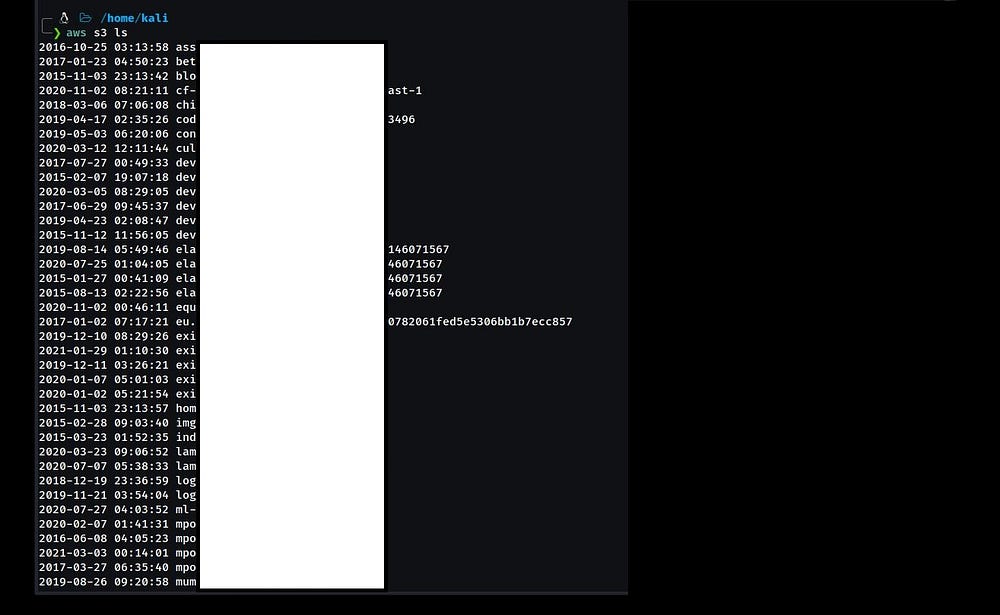
To verify those discovered AWS credentials, I configured them at ‘awscli’ program in the system terminal and tried to access their AWS S3 Storage Buckets associated with that AWS account.


KaaBOOM! I am able to list their 93 AWS S3 Buckets belonging to that organization. Using those AWS credentials, I can also access their AWS cloud infrastructure. As soon as I discovered it, I created and submitted a POC to BugéDex Team
Finally on BugBashing, I submitted 5 High & 1 Critical severity reports.
At last, in addition to those bug reports, the participants must submit a blog, expressing their experience at the workshop and about the BeVigil platform.
EDIT: In addition to those credentials discoveries, in between 3rd and 10th of October, I have discovered 7 mobile applications with hardcoded Twitter OAUTH Token and Secret & 8 apps with hardcoded Facebook OAUTH Token and Secret & 2 apps with hardcoded AWS Credentials & 1 app with hardcoded Slack Webhooks & Razorpay Key ID & Secret. All of them found to be valid. Finally, it was 25 bugs that I discovered using BeVigil application. Happy to learn & also secure those applications by responsibly reporting to them. Thanks CloudSEK & CSI-VIT Teams for the opportunity!
The scenarios when the organizations hardcode their AWS API Key & Secret,

Key Takeaways!

- ReFreshed the OWASP TOP 10 Web Application & Mobile
- Triage process in detail
- Quality Bug Report Writing
- Introduced to CloudSEK’s BeVigil
- Being Patience & Persistent. I found the hardcoded AWS cred, two days later the main event
- Different API Keys verification
Reference:
- BugéDex | The Art of Bug Bounty, Bug Bash and Reporting from Vellore Institute of Technology (VIT), Vellore // D2C (dare2compete.com)
- Streaky/keyhacks (github.com)
- BeVigil — Search engine for mobile application security testing
- Mobile Apps Exposing AWS Keys Affect 100M+ Users’ Data — BeVigil Blog
- Computer Society of India — VIT (csivit.com)
- CloudSEK | AI-powered Digital Risk Protection Software
- GIPHY — Be Animated
Credits to
Rahul Sasi | LinkedIn ~ [ Founder and Chairman @ CloudSEK ]
Authored by
IRSHAD AHAMED ( irshadahamedpro@gmail.com )
